The Evolution of Access Control and Digital Identity
.webp)
The security landscape is swiftly transforming, as technological advancements reshape how organizations oversee access and identity in the digital realm.
Let's explore the evolution of access control systems and examine the emergence of digital identity solutions. Moving forward, the emphasis is shifting. We are moving from strict physical control to more flexible systems. These systems can easily blend with personal and professional digital identities.
The Journey of Access Control: From Keys to Digital Identity
Access control systems (ACS) have significantly evolved from their origins, where replacing keys with cards was once revolutionary.
Originally, motivated by convenience, these systems have evolved into essential frameworks for protecting people, assets, and data in contemporary businesses.
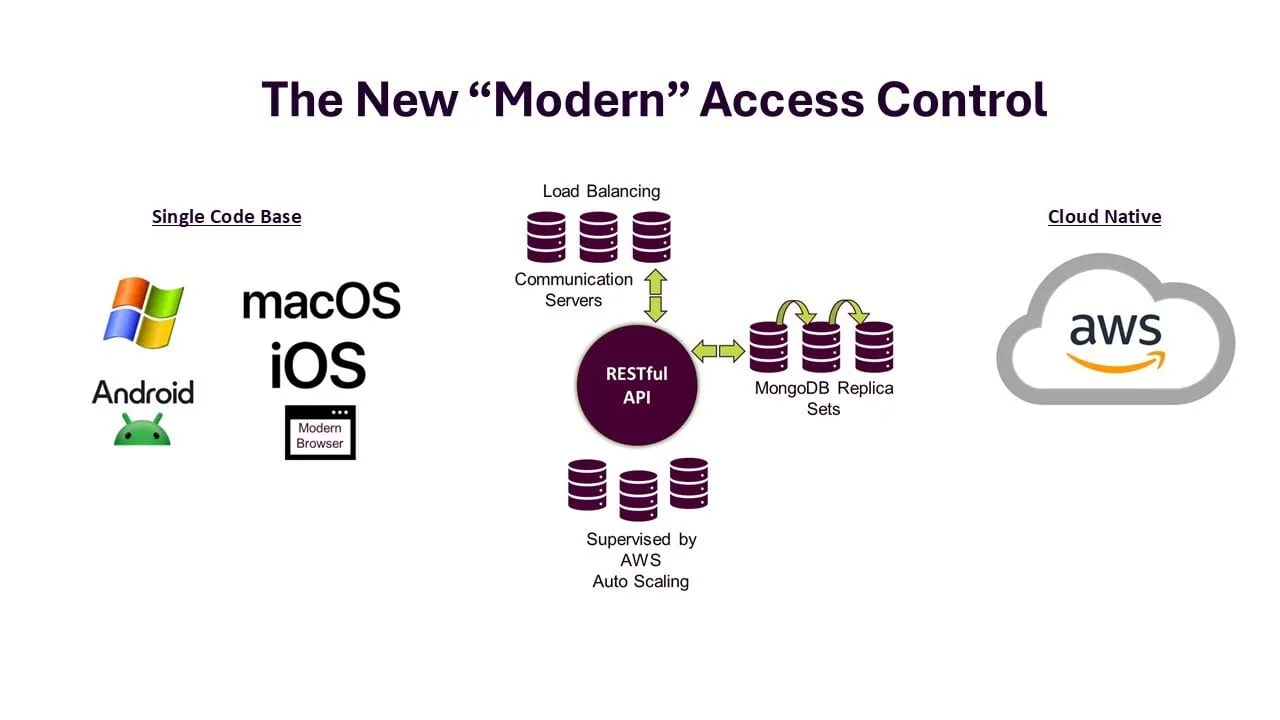
Early access control systems depended on host-based setups and proprietary hardware. In contrast, modern solutions leverage cloud technology, open RESTful APIs, open hardware, and mobile platforms, offering enhanced flexibility and integration.
A major catalyst for this evolution is the rapid pace of technological advancement. Modern businesses require adaptable solutions that can grow alongside them. Native cloud access control systems on platforms like AWS help companies reduce infrastructure management costs. They also work well with existing software.
Secure Solutions for a Hybrid World
Nowadays, security is more complex than ever, and compliance has become crucial. We need to balance physical security with the rising threat of cyber-attacks.
Organizations must follow strict cybersecurity standards like ISO 27001. They also need to keep their systems flexible to meet new challenges. These challenges include Single Sign-On (SSO), Two-Factor Authentication (2FA), and better password protocols.
The distinguishing feature of modern Access Control Systems is their seamless integration into business workflows. These systems automate tasks, reduce human error, and improve efficiency. They connect physical security with identity and access management (IAM) tools.
Learn more: Access Control in Commercial Real Estate: A Complete Guide
Automating user setup and enforcing rules helps security teams and promotes collaboration. This allows them to focus on important projects rather than just reacting to threats.
The Rise of Digital Identity: The New Frontier
As we delve deeper into the digital age, digital identity is increasingly crucial for access management. Once limited to basic username-password combinations, it has evolved into a complex system incorporating biometrics, smartcard credentials, and mobile wallets. The future of digital identity verification uses technologies like facial recognition and fingerprint scanning. These tools often work smoothly with platforms like Google, Apple, and Microsoft.
Businesses now regard digital identity as the cornerstone of contemporary access control. The merging of personal and work digital identities gives security teams the ability to manage access in different places. This includes both corporate offices and remote workspaces. Adaptability is particularly important as remote work and hybrid setups continue to rise in popularity.
Looking Ahead: Automation and Adaptability
The future of access control is rooted in automation. By automating security workflows, organizations can ensure that individuals receive the appropriate access at the right times, eliminating the need for manual supervision. Identity and Access Management (IAM) and Physical Identity and Access Management (PIAM) systems help businesses automate tasks. These tasks include background checks, issuing credentials, and reporting compliance.
The principle of "least privileged access" ensures that users get only the access they need for their roles. This helps reduce risks and improve security. As companies expand, their systems must remain adaptable and scalable, supporting new applications and integrations without the need to completely overhaul existing infrastructure.
Securing the Future
The next 30 years in access control will differ significantly from the past. As businesses increasingly integrate physical and digital security, access control systems must adapt to meet the evolving demands of modern organizations.
New advancements in digital identity, automation, and secure cloud solutions are changing security. The future of security will be more connected, more efficient, and more secure.
Access is not simply given; it is granted. This evolution in access control, driven by digital identity, will enhance not only security but also business productivity.
Conclusion
As technology continues to rapidly advance, businesses should protect their access control investment by choosing solutions that have the architecture to meet their current security needs and the ability to adapt in the future. The future of access control and digital identity is exciting. Choose systems that offer both security and efficiency while effectively safeguarding your people and assets.
Choose an access control solution that offers an intuitive user experience. Solutions with intuitive user experience result in fast adoption rates and make training easy.
Businesses need to stay updated on the latest industry changes and on the use of new technologies. Making the right choice reduces your risk. Stay ahead of the curve. Let’s work together to secure our future and grow for a safer tomorrow. The possibilities are endless.


.webp)
.png)